
Collect the latest CompTIA cs0-001 exam exercise questions and valid tips!
CompTIA latest exam tips 2020! Certificatedumps offers the latest cs0-001 exam exercise questions, cs0-001 pdf, the cs0-001 free exam to help you improve your skills! Improve the exam to pass!
Lea4pass is our partner and they have the most authoritative testing experts! Easily pass the exam, select the complete CompTIA cs0-001 exam dumps https://www.leads4pass.com/cs0-001.html The latest updated exam dump. Guaranteed to be effective and authentic! leads4pass year-round updates ensure your first exam passes!
Certificatedumps Exam Table of Contents:
- Latest CompTIA cs0-001 google drive
- Effective CompTIA cs0-001 exam practice questions
- Related cs0-001 Popular Exam resources
- leads4pass Year-round Discount Code
- What are the advantages of leads4pass?
Latest CompTIA cs0-001 google drive
[PDF] Free CompTIA cs0-001 pdf dumps download from Google Drive: https://drive.google.com/file/d/1nXg0iP-8w37qHwEws5nQjzrzhTGa1wt3
CySA+ (Plus) Cybersecurity Analyst Certification: https://www.comptia.org/certifications/cybersecurity-analyst
The CompTIA Cybersecurity Analyst (CySA+) certification verifies that successful candidates have the knowledge and skills required to
configure and use threat detection tools, perform data analysis and interpret the results to identify vulnerabilities, threats and risks
to an organization, with the end goal of securing and protecting applications and systems within an organization.
Latest updates CompTIA cs0-001 exam practice questions
QUESTION 1
A security analyst has just completed a vulnerability scan of servers that support a business-critical application that is
managed by an outside vendor. The results of the scan indicate the devices are missing critical patches. Which of the
following factors can inhibit the remediation of these vulnerabilities? (Choose two.)
A. Inappropriate data classifications
B. SLAs with the supporting vendor
C. Business process interruption
D. Required sandbox testing
E. Incomplete asset inventory
Correct Answer: CD
QUESTION 2
A company has received the results of an external vulnerability scan from its approved scanning vendor. The company
is required to remediate these vulnerabilities for clients within 72 hours of acknowledgement of the scan results.
Which of the following contract breaches would result if this remediation is not provided for clients within the time
frame?
A. Service level agreement
B. Regulatory compliance
C. Memorandum of understanding
D. Organizational governance
Correct Answer: A
QUESTION 3
Risk management wants IT to implement a solution that will permit an analyst to intercept, execute, and analyze
potentially malicious files that are downloaded from the Internet.
Which of the following would BEST provide this solution?
A. File fingerprinting
B. Decomposition of malware
C. Risk evaluation
D. Sandboxing
Correct Answer: D
QUESTION 4
A security analyst positively identified the threat, vulnerability, and remediation. The analyst is ready to implement the
corrective control. Which of the following would be the MOST inhibiting to applying the fix?
A. Requiring a firewall reboot.
B. Resetting all administrator passwords.
C. Business process interruption.
D. Full desktop backups.
Correct Answer: D
QUESTION 5
A company office was broken into over the weekend. The office manager contacts the IT security group to provide
details on which servers were stolen. The security analyst determines one of the stolen servers contained a list of
customer PII information, and another server contained a copy of the credit card transactions processed on the Friday
before the break-in. In addition to potential security implications of information that could be gleaned from those servers
and the rebuilding/restoring of the data on the stolen systems, the analyst needs to determine any communication or
notification requirements with respect to the incident. Which of the following items is MOST important when determining
what information needs to be provided, who should be contacted, and when the communication needs to occur.
A. Total number of records stolen
B. Government and industry regulations
C. Impact on the reputation of the company\’s name/brand
D. Monetary value of data stolen
Correct Answer: B
QUESTION 6
A cybersecurity analyst has several SIEM event logs to review for possible APT activity. The analyst was given several
items that include lists of indicators for both IP addresses and domains. Which of the following actions is the BEST
approach for the analyst to perform?
A. Use the IP addresses to search through the event logs.
B. Analyze the trends of the events while manually reviewing to see if any of the indicators match.
C. Create an advanced query that includes all of the indicators, and review any of the matches.
D. Scan for vulnerabilities with exploits known to have been used by an APT.
Correct Answer: B
QUESTION 7
Which of the following describes why it is important for an organization\’s incident response team and legal department
to meet and discuss communication processes during the incident response process?
A. To comply with existing organization policies and procedures on interacting with internal and external parties
B. To ensure all parties know their roles and effective lines of communication are established
C. To identify which group will communicate details to law enforcement in the event of a security incident
D. To predetermine what details should or should not be shared with internal or external parties in the event of an
incident
Correct Answer: A
QUESTION 8
A security analyst, who is working for a company that utilizes Linux servers, receives the following results from a
vulnerability scan:
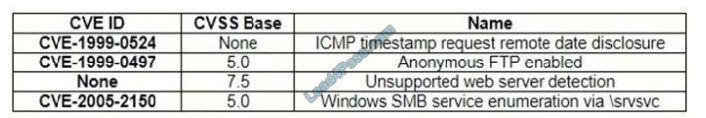
Which of the following is MOST likely a false positive?
A. ICMP timestamp request remote date disclosure
B. Windows SMB service enumeration via \srvsvc
C. Anonymous FTP enabled
D. Unsupported web server detection
Correct Answer: B
QUESTION 9
When reviewing network traffic, a security analyst detects suspicious activity:
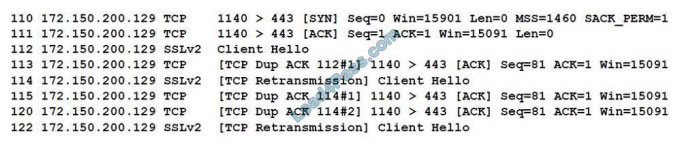
Based on the log above, which of the following vulnerability attacks is occurring?
A. ShellShock
B. DROWN
C. Zeus
D. Heartbleed
E. POODLE
Correct Answer: E
QUESTION 10
The Chief Information Security Officer (CISO) has decided that all accounts with elevated privileges must use a longer,
more complicated passphrase instead of a password. The CISO would like to formally document management\’s intent
to set this control level. Which of the following is the appropriate means to achieve this?
A. A control
B. A standard
C. A policy
D. A guideline
Correct Answer: C
QUESTION 11
A system administrator has reviewed the following output:
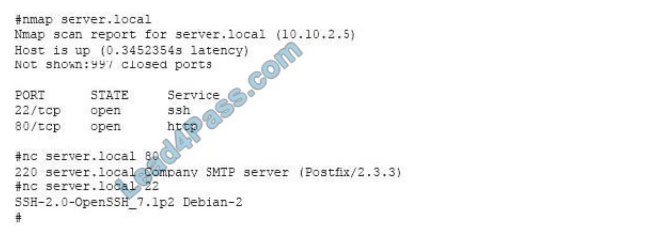
Which of the following can a system administrator infer from the above output?
A. The company email server is running a non-standard port.
B. The company email server has been compromised.
C. The company is running a vulnerable SSH server.
D. The company web server has been compromised.
Correct Answer: A
QUESTION 12
Considering confidentiality and integrity, which of the following make servers more secure than desktops? (Select
THREE).
A. VLANs
B. OS
C. Trained operators
D. Physical access restriction
E. Processing power
F. Hard drive capacity
Correct Answer: BCD
QUESTION 13
A security analyst was asked to join an outage call for a critical web application. The web middleware support team
determined the webserver is running and having no trouble processing requests; however, some investigation has
revealed firewall denies to the web server that began around 1.00 a.m. that morning. An emergency change was made
to enable the access, but management has asked for a root cause determination. Which of the following would be the
BEST next step?
A. Install a packet analyzer near the webserver to capture sample traffic to find anomalies.
B. Block all traffic to the webserver with an ACL.
C. Use a port scanner to determine all listening ports on the webserver.
D. Search the logging servers for any rule changes.
Correct Answer: D
Related CompTIA cs0-001 Popular Exam resources
| title | youtube | CompTIA | leads4pass | leads4pass Total Questions | |
|---|---|---|---|---|---|
| CompTIA CySA+ | leads4pass cs0-001 dumps pdf | leads4pass cs0-001 youtube | CySA+ (Plus) Cybersecurity Analyst Certification | https://www.leads4pass.com/cs0-001.html | 416 Q&A |
| leads4pass cs0-002 dumps pdf | leads4pass cs0-002 youtube | CySA+ (Plus) Cybersecurity Analyst Certification | https://www.leads4pass.com/cs0-002.html | 69 Q&A |
Latest leads4pass Year-round Discount Code 2020

Why leads4pass is the industry leader
leads4pass has many years of exam experience! Finishing school is your goal! Getting good employment conditions is your goal!
Our goal is to help more people pass the CompTIA exam! Exams are a part of life but important!
In the study you need to make great efforts to sum up the study! Trust leads4pass if you can’t easily pass because of exam details!
We have the most authoritative CompTIA exam experts! The most efficient pass rate! We are the industry leader!
Latest update leads4pass cs0-001 exam dumps: https://www.leads4pass.com/cs0-001.html (416 Q&As)
[Q1-Q12 PDF] Free CompTIA cs0-001 pdf dumps download from Google Drive: https://drive.google.com/file/d/1nXg0iP-8w37qHwEws5nQjzrzhTGa1wt3
Summarize:
This blog shares the latest CompTIA cs0-001 exam dumps, cs0-001 exam questions, and answers! cs0-001 pdf, cs0-001 exam video!
You can also practice the test online! leads4pass is the industry leader!
Select leads4pass cs0-001 exams Pass CompTIA cs0-001 exams “CompTIA CSA+ Certification Exam”. Help you successfully pass the cs0-001 exam.